Configuring OneLogin as an SMA Authentication Server
Description
This article provides step-by-step instructions to configure SonicWall Secure Mobile Access 1000 series appliance with OneLogin cloud-based Identity Provider.
Resolution
Prerequisites
SAML being time-sensitive protocol, enable NTP service on SMA appliance (Services -> Network Services -> NTP) to avoid any time related issues.
To add the SMA application to the OneLogin service:
- Choose Applications -> Applications top-menu.
- Click on the Add App button.
- Search for Sonicwall VPN and select Sonicwall VPN (SAML2.0) application.
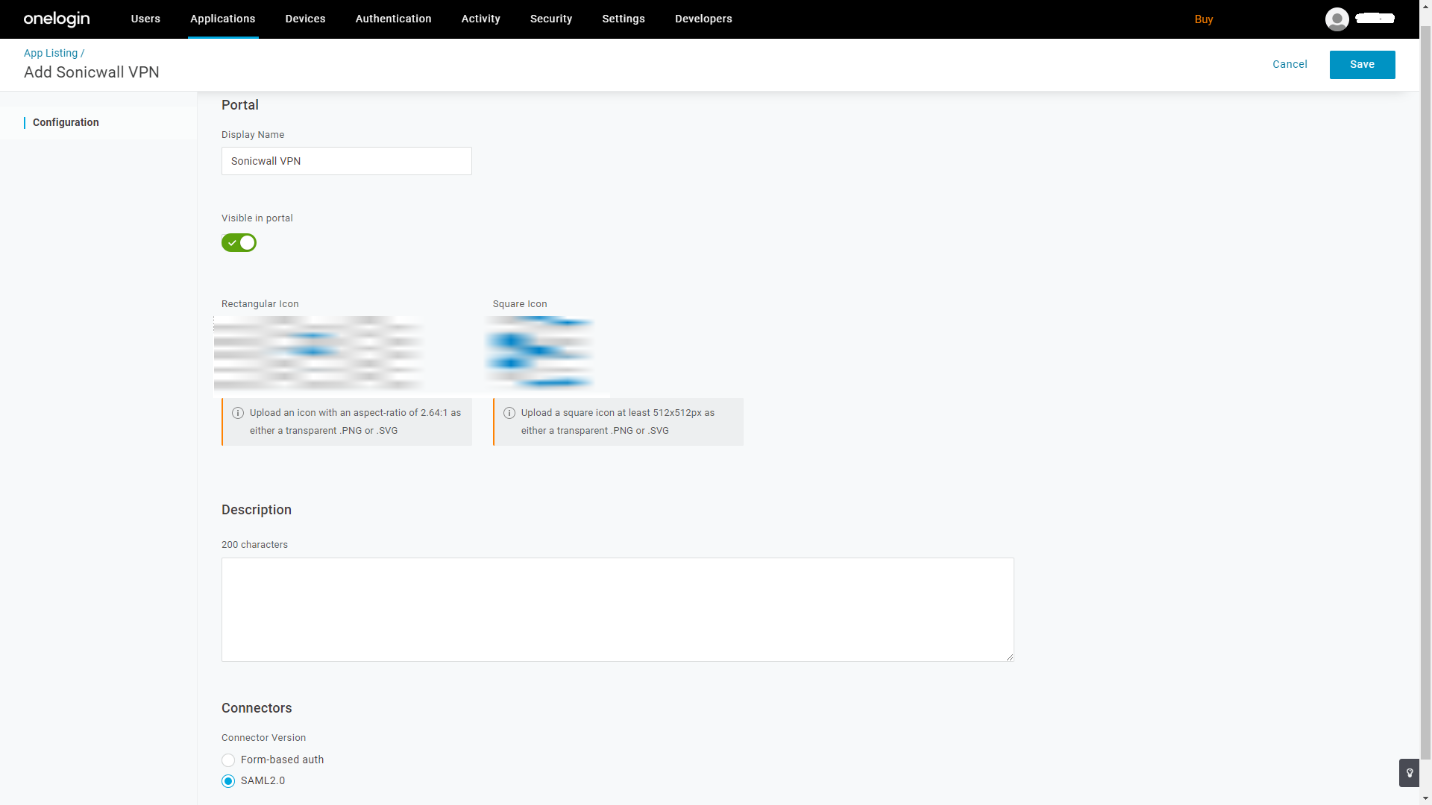
- Provide a friendly application name.
- The logo can be changed.
- Click on the Save button at the top-right corner.
- Open Configuration menu again.
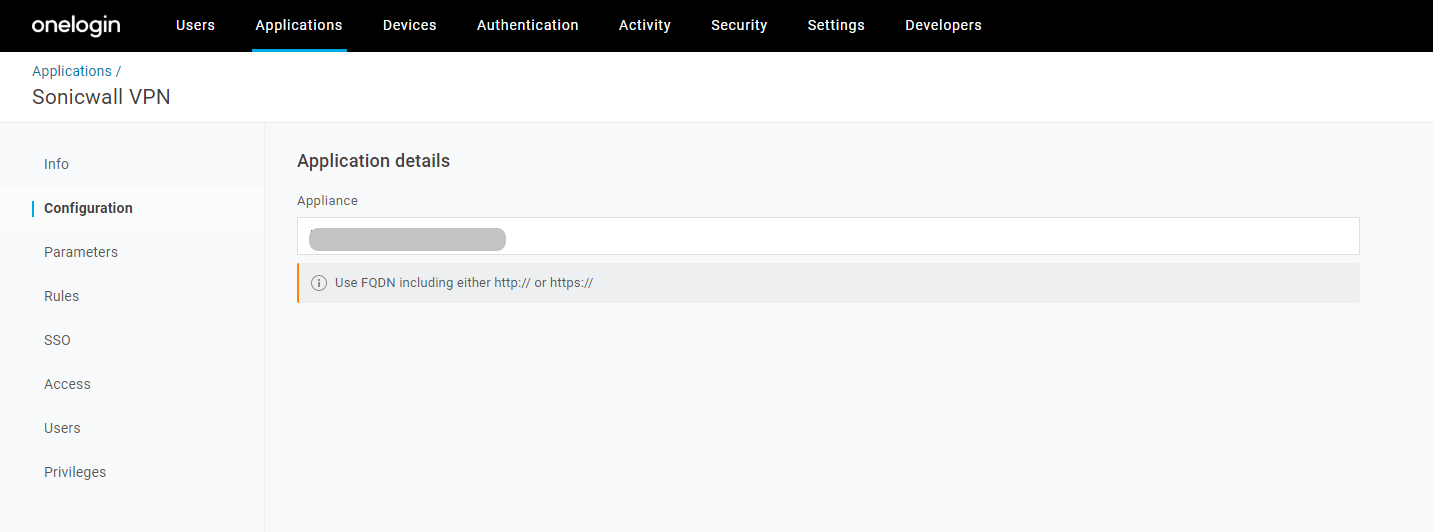
- Under Appliance details, provide Workplace FQDN without a trailing slash (Eg: https://vpn.example.com) (Note: This configuration should match the Endpoint FQDN configuration chosen under SAML Authentication server at SMA-1000 appliance.)
- Click on the Save button.
- Click on the SSO option on the left menu.
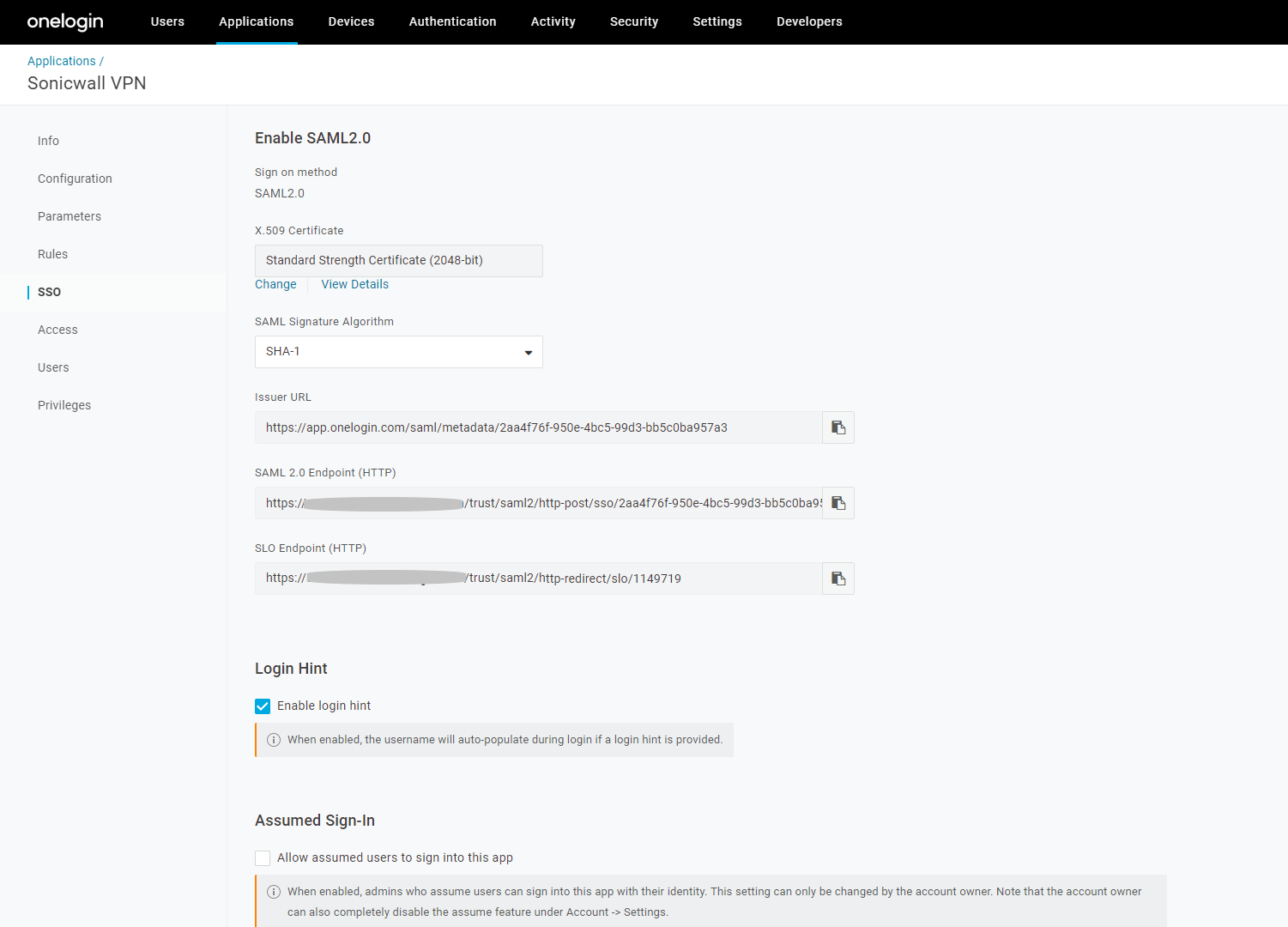
- Under X.509 Certificate section, right-click on View Details and open on new window.
- Now, under X.509 Certificate, select X.509 PEM option and download the certificate.
- Go back to application browser tab.
- Note Issuer URL value.
- Note SAML 2.0 Endpoint (HTTP) value.
To configure OneLogin as an SMA Authentication Server:
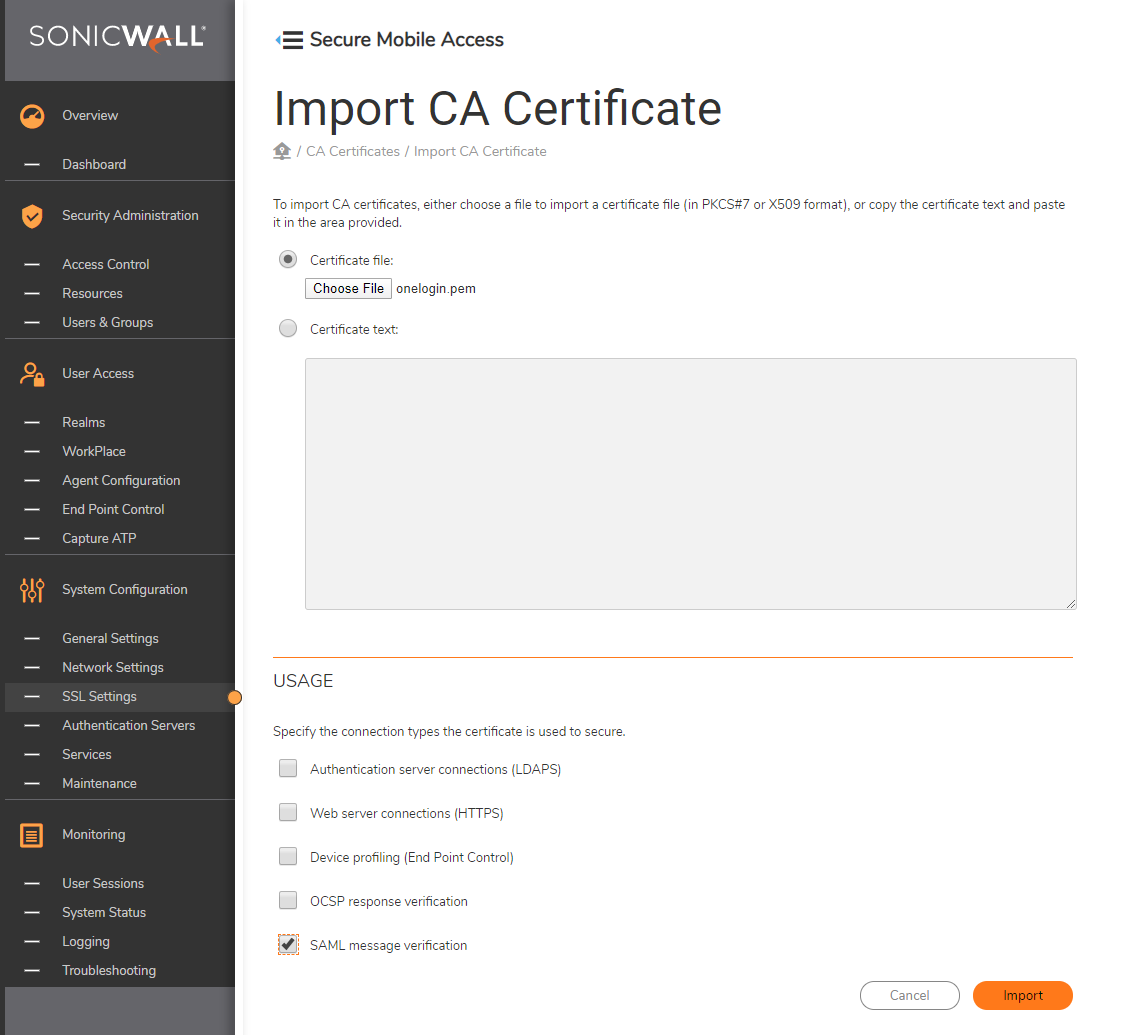
To upload the OneLogin PEM certificate downloaded from OneLogin portal,
- Go to SSL Settings -> CA Certificates -> certificates -> Edit.
- Select the OneLogin certificate file.Before importing, under USAGE section, select SAML message verification option and disable all other options.
- Click Import button.
Make a note of the certificate name.
To Configure OneLogin as authentication server,
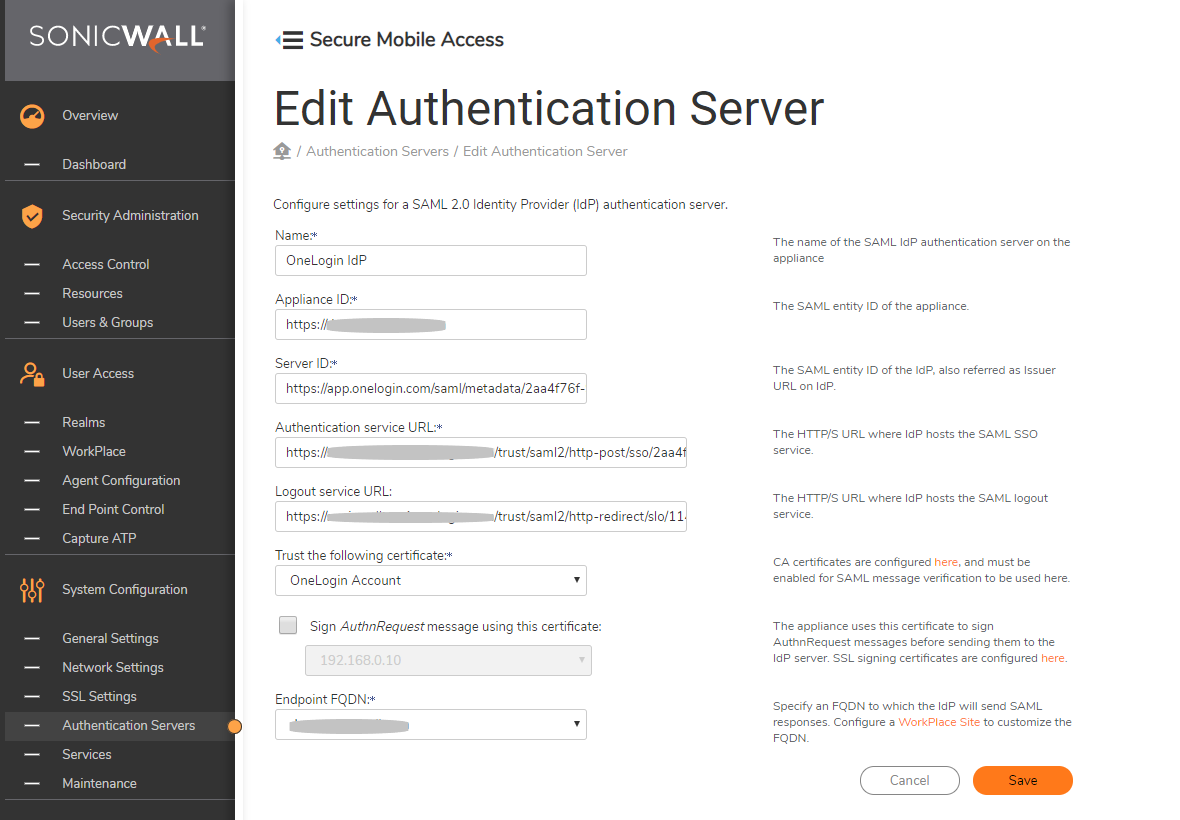
- Click Authentication Servers on left pane-> Click New.
- Select SAML 2.0 Identity Provider under the USER STORE.
- Add a friendly name for OneLogin SAML IdP.
- Add the Appliance ID of OneLogin (Eg: https://vpn.example.com) with no trailing slash.
- Add Server ID as Issuer URL value noted from OneLogin configuration.
- Add the Authentication service URL as SAML 2.0 Endpoint (HTTP) value noted from OneLogin configuration.
- Logout service URL is optional - configure this option if the user has to log out from OneLogin after logging out of SMA.
- Under Trust the following certificate select OneLogin certificate.
- Under Endpoint FQDN, select the FQDN that is provided at OneLogin (vpn.example.com).
- Click Save and apply the pending changes.
This SAML authentication server can be used in a realm for authentication.
Related Articles
not finding your answers?